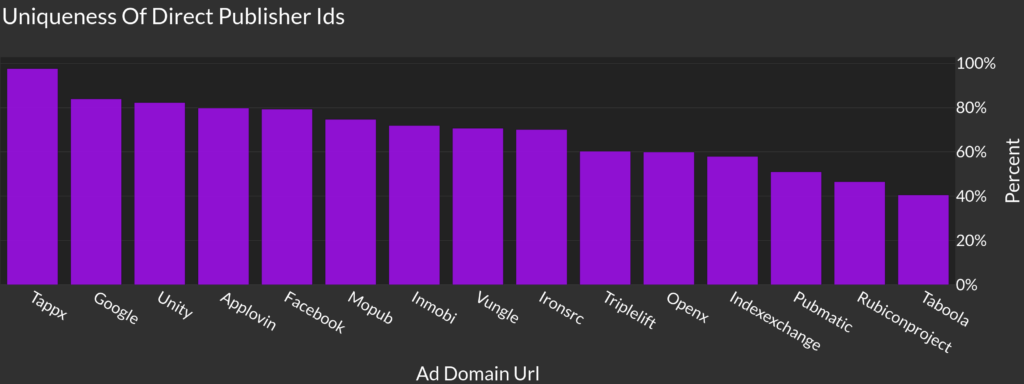
Looking around app-ads.txt files one of the first things I was excited to check was whether DIRECT publisher IDs show up on other unrelated apps. To do this I ignored any apps that shared the same developer contact URL or Developer IDs. This doesn’t catch 100% of the legitimate publishers I checked, as the examples to follow show, but does provide a good rough estimate of which networks seem to have publishers whose IDs are more mixed.
DIRECT traffic should mean that your app controls the publisher ID listed. But sometimes when looking through ads-txt there are publisher IDs that appear many time on unrelated apps. This could mean that an ad buyer could be buying ads from more than just the app they were intending, which means both good and bad quality could be mixed together.
The worst possible use case is a bad actor ad network mixing unrelated publishers together, then asking each of them to use the DIRECT tag. It turns out this is much less obvious than I first assumed, but it does seem like certain networks do have a higher prevalence of mixed IDs. Let’s look at some examples.
Number 1: Quiz Game(s)


One of the first examples I looked at was Blackpink Quiz Game who’s Unity, Google and other publisher IDs were shared across hundreds of other apps like this Family Guy-Quiz. As you can see, the two titles visually look quite similar. Each of these hundreds of apps belonged to different Google Play developers each with their own developer ids.
In addition to being visually similar, they also the same top level domain hosting their developer page url. For example Blackpink: http://pub-nbzaw-b7jg6.quickappninja.com/ and Family Guy-Quiz: http://pub-9j4jn-zu5k3.quickappninja.com/
Each link does host it’s own app-ads.txt file, but they were nearly identical across each app, containing the same DIRECT and RESELLER publisher IDs. Looking at the top level domain we see that QuickApp is an online tool that lets you create quize games from your browser. When you export the APK from the site it would likely all contain the same ad monetization accounts, controlled by QuickApp. QuickApp does later share some of the ad revenue back to the original creator.
To sum up, while that is an interesting business model, it certainly is not the kind of ad fraud I was originally looking for, and for now I’ll leave this as undecided for how to handle it.
Number 2: Crazy Marvin
Next try found another Unity ID that showed across a hundred plus apps. Checking the apps I didn’t immediately see a pattern this time. One a Dragon Ball Z game by Yodo1, a large game publisher, while the others were smaller other games with different styles and developers. Most of the developers did have several games.
com.PoisonGames.ROEQ
rocks.poopjournal.pimplepopper
com.jk.us.bullet.train.simulator
I found it really interesting that the oddest of the titles, Pimple Popper, had a GitHub linked with it’s game open sourced with a group of people working on it. So I reached out to Crazy-Marvin the dev of the Pimple Popper game to see if he could lend some insight.
Marvin was very helpful and wrote back immediately to let me know he didn’t know much about ads, but that he had been contacted by Yodo1 and per their request put the relevant ad SDKs and app-ads.txt file on his site.
Again, this seems to be a monetization partner who runs ads on behalf of the client, but without taking over their developer page or showing any other obvious links.
Number 3: rubiconproject.com, 24400, DIRECT
https://famcast.co.za/app-ads.txt
rubiconproject.com, 24400, DIRECT, 0bfd66d529a55807
rubiconproject.com, 24400, RESELLER, 0bfd66d529a55807Finally I found one that looks more suspicious than the others. This ID 24400 is located in 500+ separate developer sites meaning 1000s of apps are pointed to this publisher ID as DIRECT traffic. Oddly, it is almost always paired with a RESELLER line with the same ID. RESELLER here would be fine, as it is being resold, but DIRECT seems highly unlikely. Looking through the apps again they all appear to be unrelated.
Compared to the first and second attempt, Rubicon is not a SDK ad network, but a programmatic SSP.
Outcome: Inconclusive, but a picture is starting to form
While there is a lot of different ways we can put together our monetization accounts, there do seem to be a higher prevalence of mixed/shared IDs on the programmatic only traffic such as Rubicon, PubMatic, IndexExchange. Looking again at our plot from the beginning, highlighting the traditional networks that do both buying and selling, we do see that they tend to rank higher than the pure programmatic SSPs.
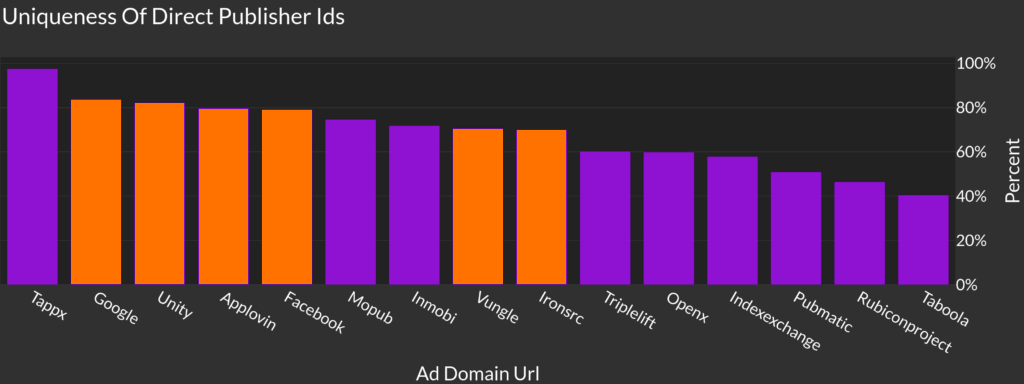
Next?
I think that the results are pretty inconclusive, but do show some directions to move forward. I learned that there are quite a few situations where shared DIRECT publisher IDs is a natural outcome of some company’s revenue setup, but still some situations appear to be incorrectly labeled publisher IDs. The networks that do have these shared publisher IDs seem to be more prominently programmatic SSPs.
Do you have any specific examples you’d like me to check? Feel free to comment or send me your developer URL and I can help look into your IDs. Do you think there is interest in a tool to help check your app-ads.txt for network quality?