Looking to add traffic analysis to my free mobile app intelligence platform AppGoblin, I needed to get an emulator up and running with a way to track the HTTPs traffic leaving the app.
I’ve done this a couple years now, writing down my notes in github.com/ddxv/mobile-network-traffic and it never seems to get any easier 🥲, but at least this year it seemed like I needed fewer tools.
So, if you just want the technical steps head to github.com/ddxv/mobile-network-traffic. This blog post will be a higher level overview.
Android Emulator: Waydroid
Waydroid is an open source Android emulator which runs on the Linux desktop environment Wayland. Wayland is now the default for many popular distros surpassing X11, so getting Waydroid up and running is VERY easy now.
Bypassing Android certificates authority
This is the trickiest step. Android, by necessity, wants to make it very difficult to install a custom CA which will allow decrypting the HTTPs traffic later with a man in the middle (MITM). In this case, since Waydroid is an emulator running on my laptop, the “man in the middle” is my laptop itself. This makes it very easy to catch and handle the traffic since I can easily edit my own laptops network with iptables
To bypass the CA we need to install Magisk with a custom script that will tell the Android operating system to trust a manually installed CA. The CA is the CA of the MITM, so it can display the traffic in clear text.
Proxy: mitm-proxy
Of all the parts, this one seems to never change. It’s a pretty rock solid and well managed open source python project that gives you a browser UI to see the traffic leaving a device.
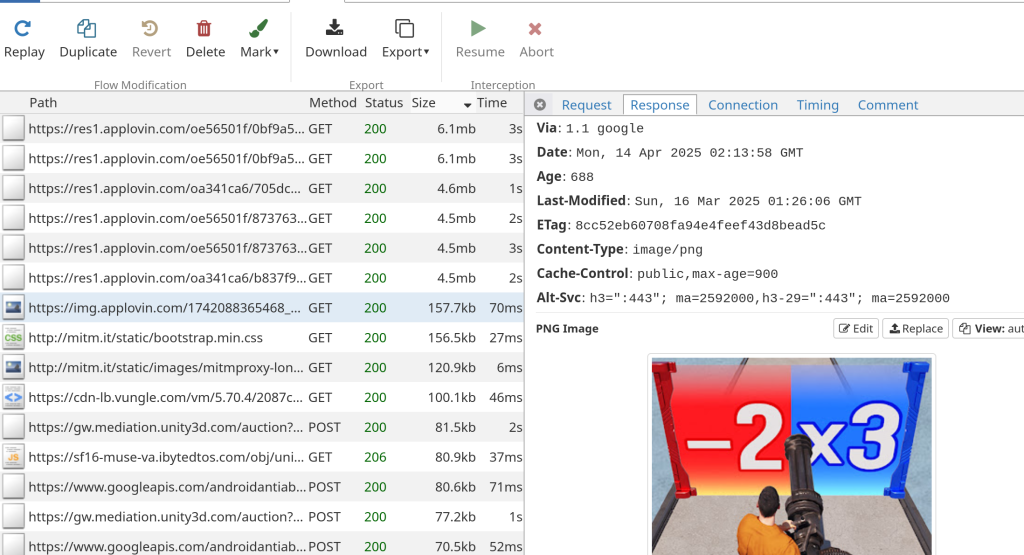
Here you can see the various ad requests to Google / AppLovin / Vungle and the responding ad resource.
Next
Now it’s time to work on recording this, tagging, storing the data and trying again with another app. If you have any advice or ideas feel free to reach out.