I de-compiled TikTok (“com.zhiliaoapp.musically” v33.3.3 from Feb 2nd, 2024) from ApkPure.net and noticed that the way it called AppsFlyer looked a bit different than what I expected and quickly led me to a GitHub issue which makes it seem like they are using an outdated way to collect install information from Google Play which may…
Tag: security
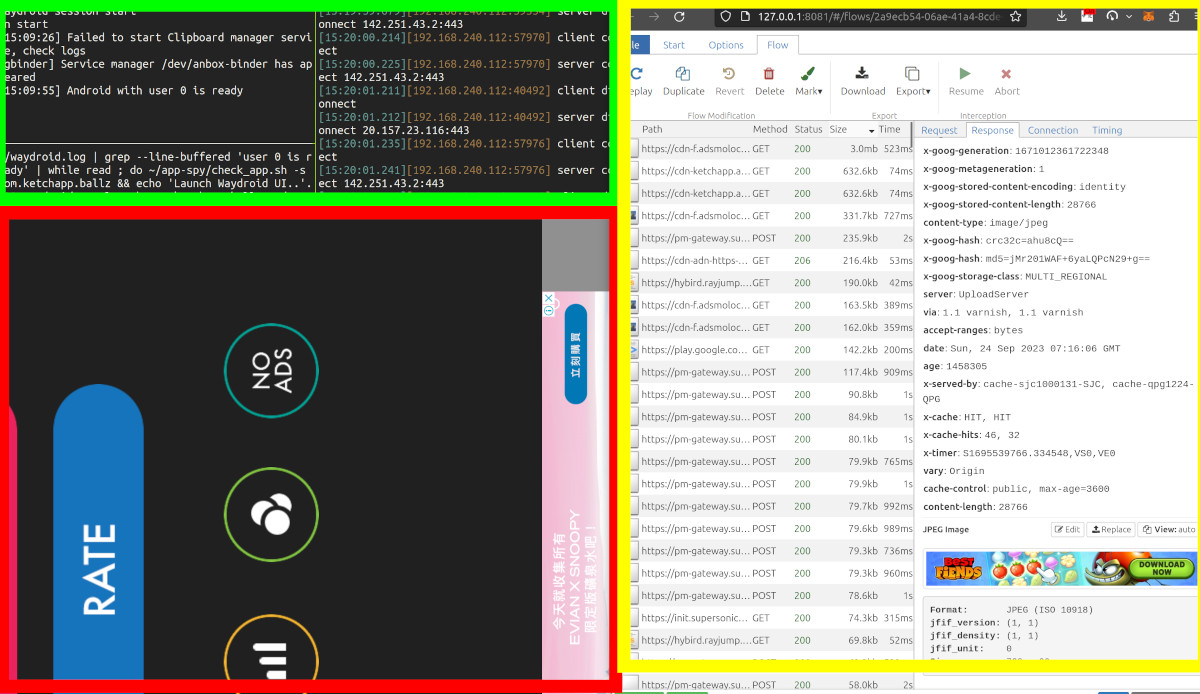
How to see traffic from your Android Device
GREEN: background processes for emulator and mitmproxy. RED: Running game (portrait but on side) with a pink banner ad at bottom. YELLOW: mitmproxy captured traffic with another example banner ad.