For a week or two I’ve been working on updating the appgoblin.info top ad networks and MMPs. Currently both are still up, which should change but I’ll give an overview of the process of changing and what might be next up. Goal: Display the top clients I’ve long wanted to have a way to view…
What does DIRECT mean for App-Ads.txt?
Recently I started working on a project on appgoblin to estimate the number of client apps for all mobile advertising and data collection companies. In doing this there are currently two sources of data: decompiled SDKs of which I have only done ~20k apps and app-ads.txt which I have scraped closer to ~200k apps’ app-ads.txt…
Svelte 5 Data Table Comparisons
While working on a new analytics dashboard I wanted to find a good table tool manage my table like data from the backend. My main goal is to have dynamic group by for the table’s dimensions. While this has been something that I’ve always liked about Python based backends, it definitely wasn’t something I found…
How to figure out which 3rd Parties might be integrated with an iOS App?
In the past couple months I built out scraping for Android apps which downloads, decompiles, scrapes the `AndroidManifest.xml` then analyzes the Android app for known 3rd party ad networks or trackers. I enjoyed this a lot, but the other half of the equation, iOS remained elusive. I was surprised how much more difficult this turned…
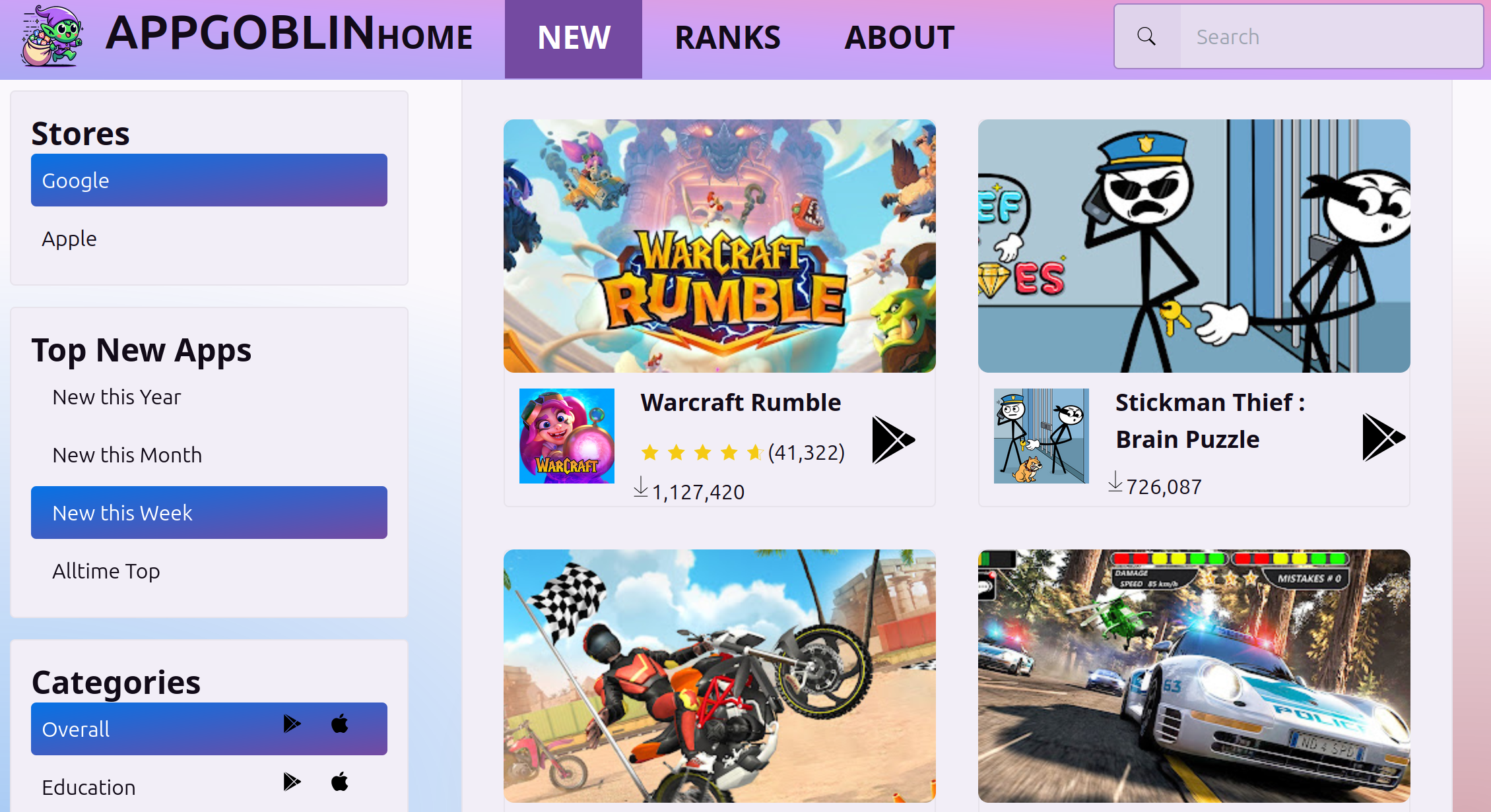
See which MMPs and Networks Apps and Games are Using
I recently added a free feature to AppGoblin to see which advertising/monetization ad networks and MMP partners apps are using. You can break down the results by category and and group by parent companies. The data is pulled from the top ~10k Android apps, which I downloaded, de-compiled and examined their AndroidManifest.xml to determine which…
Is this a TikTok security vulnerablity for ad fraud?
I de-compiled TikTok (“com.zhiliaoapp.musically” v33.3.3 from Feb 2nd, 2024) from ApkPure.net and noticed that the way it called AppsFlyer looked a bit different than what I expected and quickly led me to a GitHub issue which makes it seem like they are using an outdated way to collect install information from Google Play which may…
Before You Agree: What data does TikTok collect before Terms of Service?
Would you like to see what data is coming out of TikTok when you first open it up? Let’s get to it. Didn’t this used to be easy to do? As security for iPhones and Androids increased it continually made viewing the traffic leaving your own device more difficult. This is in stark contrast to…
ClickHouse: Refreshing Take on Materialized Views
Working on my Open Source MMP I have been seeing how much of it will work with ClickHouse. Unfortunately combining multiple streaming data sources in ClickHouse was proving difficult as data would semi randomly not join correctly. This led to a potential fix by using the very recent ClickHouse refreshable materialized views. These refreshable views…
AppGoblin: Free App Stats & Info
The past few weeks I spent building a front-end for an app store crawler that I made. The end goal is just to provide an open front-end for the apps details for the approximate 2.5m apps (already 1/2 those are no longer live) I’ve crawled from the Google & Apple stores. The site is now…
Keeping Mobile Gamers Engaged with App Widgets
I love using widgets. I probably have too many of them on my phone’s home screen. News apps, weather apps, stocks, stats. I love being able to glance through them without opening the corresponding apps. This led me to realize though that I have seen very few widgets for mobile games. As I started working…